top of page

Blog


Certified Red Team Professional (CRTP)
All you want to know about Certified Red Team Professional (CRTP) by Altered Security.
Nikhil Mittal
Apr 18, 20233 min read


Feature Abuse: Recovering Deleted Storage Accounts to Extract Secrets
Hello everyone! Recently, I have been working on developing some interesting Azure security challenges. I came across something...
Nagendrra C
Feb 14, 20235 min read

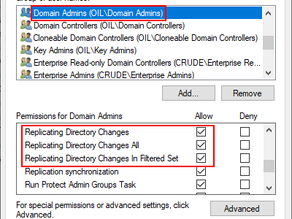
A primer on DCSync attack and detection
Hello All, Active directory is a backbone of almost all the organizations. It helps the IT team to manage the systems, users, policies...
Chirag Savla
Feb 16, 20228 min read
bottom of page




